In the fast-paced world of cryptocurrencies, security isn’t just a buzzword—it’s your absolute top priority. Whether you hold a fraction of Bitcoin or a diverse portfolio, your digital assets can vanish in seconds without the proper precautions. Therefore, the first and most crucial step for any responsible investor is creating a truly secure crypto wallet.
This in-depth guide will reveal what a crypto wallet is, explore the different types, and give you a step-by-step blueprint to protect your digital wealth. Ultimately, you’ll be able to master the art of crypto security and never lose sleep over your investments again.
Understanding the Basics: What is a Crypto Wallet?
Think of a crypto wallet not as a place where your coins are physically stored, but rather as your digital key ring. It’s where your private keys are securely held. In other words, these keys function as the “password” you need to access and move your funds on the blockchain.
It’s important to clarify that your coins don’t exist in the wallet itself; instead, they are recorded on a public, immutable ledger called the blockchain. Consequently, the wallet simply holds the cryptographic proof that you are the rightful owner of those coins.
Choosing Your Security Level: Hot vs. Cold Wallets
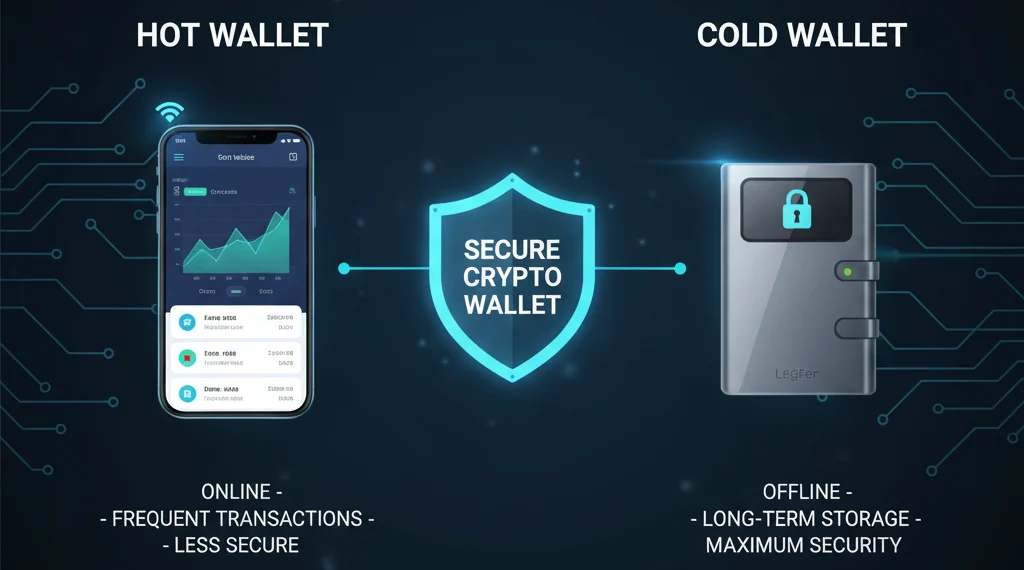
Before you even begin, it’s crucial to understand the two main categories of wallets: “hot wallets” and “cold wallets”. Each has distinct advantages and, conversely, its own set of trade-offs.
Hot Wallets: Fast and Convenient
To begin with, let’s define hot wallets. These are wallets that are actively connected to the internet. For instance, popular examples include mobile apps like Trust Wallet and MetaMask, or the wallets provided by major crypto exchanges. As a result, they are highly convenient and ideal for frequent traders and quick, everyday transactions. However, this convenience comes at a cost; they are more susceptible to cyber-attacks, phishing scams, and malware. In fact, hot wallets are the most common targets for hackers.
Cold Wallets: The Ultimate Security Vault
In contrast, cold wallets are devices that are not connected to the internet. Typically, this includes hardware wallets like Ledger and Trezor, or even a simple paper wallet. The main advantage is maximum security, making them perfect for long-term storage of large amounts of crypto. On the other hand, they are less convenient for day-to-day transactions.
A Step-by-Step Blueprint for Creating a Secure Crypto Wallet
Follow these essential steps to build a fortress around your crypto.
1. Choose the Right Wallet Type for Your Needs Your choice ultimately depends on your specific needs. For example, if you plan to make many frequent trades, a reliable hot wallet is a good starting point. Conversely, if your objective is to save your cryptocurrencies for months or years, a cold wallet is an absolute necessity.
2. Download from Official Sources Only Remember that phony wallets are a common scam designed to steal your funds. Therefore, for mobile apps, only download from the official App Store or Google Play Store. Furthermore, always verify the developer. Similarly, for hardware wallets, buy directly from the manufacturer’s official website or an authorized reseller. Never, under any circumstances, buy from third-party marketplaces like eBay or Amazon.
3. The Golden Rule: Back Up Your Seed Phrase When you create your wallet, you will receive a seed phrase (typically 12 or 24 words). This phrase is the master key to your funds. Consequently, you must never take a screenshot, save it in an email, or store it on the cloud. Instead, write it down on a piece of paper, or even on a metal plate, and store it in a secure location like a safe. After all, this phrase is the only way to recover your wallet if you lose your device.
4. Activate Two-Factor Authentication (2FA) If your wallet or exchange offers 2FA, enable it immediately. In fact, this adds an essential layer of security, requiring a unique code from an app like Google Authenticator or Authy to access your account.
5. Protect Your Devices as a First Line of Defense Your device is the gateway to your crypto. As such, you must keep its operating system and all apps up to date. Moreover, never access your wallet on public Wi-Fi networks. Lastly, use unique, complex passwords for every service you use.
6. For Large Amounts, Hardware Wallets Are the Best Option Ultimately, if you’re serious about crypto, a device like the Ledger Nano X or Trezor Model T is a must-have. Due to the fact that they keep your private keys completely offline, these devices make it virtually impossible for remote hackers to steal your funds.
Pro-Level Security Tips to Stay Ahead
- Diversify: Additionally, for significant amounts, consider using more than one wallet.
- Be Discreet: Likewise, never share screenshots of your balances or discuss your holdings publicly.
- Regular Audits: Furthermore, periodically check your seed phrase backup and update the firmware on your hardware wallets.
Final Thoughts: Take Control of Your Crypto Future
Creating a secure crypto wallet is straightforward but requires meticulous attention to detail. To summarize, by choosing the right solution, safeguarding your seed phrase, enabling 2FA, and protecting your devices, you’re taking essential steps to secure your investments.
Finally, remember the most important lesson in crypto: your security is your responsibility. As the community often says, “Not your keys, not your coins.” This powerful saying highlights the fact that if you don’t control your private keys, you don’t truly own your crypto.